Why we invested in Nudge Security
Why cybersecurity needs a big nudge
By Roger Thornton, General Partner
Executive Summary
Nudge Security emerged from stealth today with the first-ever SaaS security solution to discover shadow IT and curb SaaS sprawl across devices and locations. Nudge Security does what previous enterprise security solutions have failed to do: they make employees part of the solution.
The problem Nudge Security solves ultimately derives from consumer behavior on the internet. Consumers have been conditioned for years to trade valuable personal information for “free stuff” online. This is how the consumer internet works, and it’s the basis for an explosion of crime involving identity takeover in the physical and virtual world. This also creates chaos and havoc for corporations when their employees bring these consumer habits and services to work – creating a so-called “shadow IT” problem.
Initial feedback from a broad collection of CISOs and security practitioners indicates that this is a major pain point growing within companies of all sizes.
Consumerization of the Enterprise & Shadow IT – Chaos for the CISO
Cybersecurity threats thrive on change. The greater the change, the greater the opportunities for criminals, spies and military organizations engaged in offensive cyber operations. Change underlying technology, and the adversary will find vulnerabilities and gaps that were not obvious when things were on the drawing board. Transform the physical world into a digital one, and adversaries take advantage of the ability to reach valuable things from keyboards all around the world.
As changes take place, we see over and over again how the “old ways” of protecting things just don’t work in the new world. For example, the old notion of protecting things by creating walls around a perimeter served us well for many centuries – some might even have worked for a while in cybersecurity, but that strategy fell apart with cloud computing, mobile workforces and a myriad of other changes in the workplace.
We are in the middle of a security renaissance and period of acceptance that end users and systems of all types will eventually come under attack. New “zero trust” approaches to identity, authentication, data and the myriad of traditional network and endpoint controls are helping the CISO maintain some degree of visibility and control.
There is, however, another sweeping change already underway that involves the fundamental ways in which people work. These changes have increased employee satisfaction and productivity dramatically, but cause genuine headaches for IT and security teams. We are seeing the technology that empowers workers migrating from a small number of vendors carefully vetted, selected and managed by the company to a large and constantly changing ecosystem of SaaS solutions brought into the enterprise by the employees. A symptom of this change is commonly referred to as “shadow IT.”
The change is the modern workforce.
Over the last decade, going to work has taken on a rapidly changing form for nearly all knowledge workers. When you “go to work,” you may be at home or at a cafe or may even be in an office. When you run into questions and problems, you go online and search. When you do, you find tons of information and many cool little tools and SaaS services targeting people just like you at a time of need. Want to invite people to a marketing event? There is a SaaS service for that. Need help coming up with a logo design? There is a service for that, too. Need help filling out your expense report? There is an app for that. Needless to say, we could go on forever with all the possible problems that are solved with SaaS services and mobile apps.
That sounds like a wonderful world, particularly if you remember the stone ages and the iron curtain of computing maintained by IT departments. Back then, it was: “Want to invite people to a marketing event? Fill out a project initiation form and submit the business justification. Wait 8 weeks and then talk to a subject matter expert to contact you to create a requirements document and project plan.” Sadly that is 100% really how things worked.
The new world is amazing. What’s even more amazing is that half of this stuff is “free.” But nothing in this world is really free. Apple offers a great summary of what free entails in their privacy policy. If the service is “free,” you are not the customer – you are the product. Nonetheless, if you are trying to get something done and there is a service that has risen to the top of a competitive marketplace because it works well, you are likely to give it a try even if it costs a little money. The consumer marketplace is full of “free” services that, at best, sell you as a marketing lead and, at worst, steal your information or unlawfully access your computer. In the business world, there aren’t so many outright unscrupulous characters offering services to employees, but plenty of ones that are not “enterprise grade.”
A great example of this can be found in the cool little tool for developers called “CodeCov.” It is also a quintessential example of what can go wrong. Like thousands of other so-called freemium products available online, CodeCov is “free” to get started, and then offers a price that can be easily charged to an employee’s expense report and eventually works its way into the company with the great leverage that “the employees have already selected it.” Good luck to a CIO or CISO who wants to block it at that point.
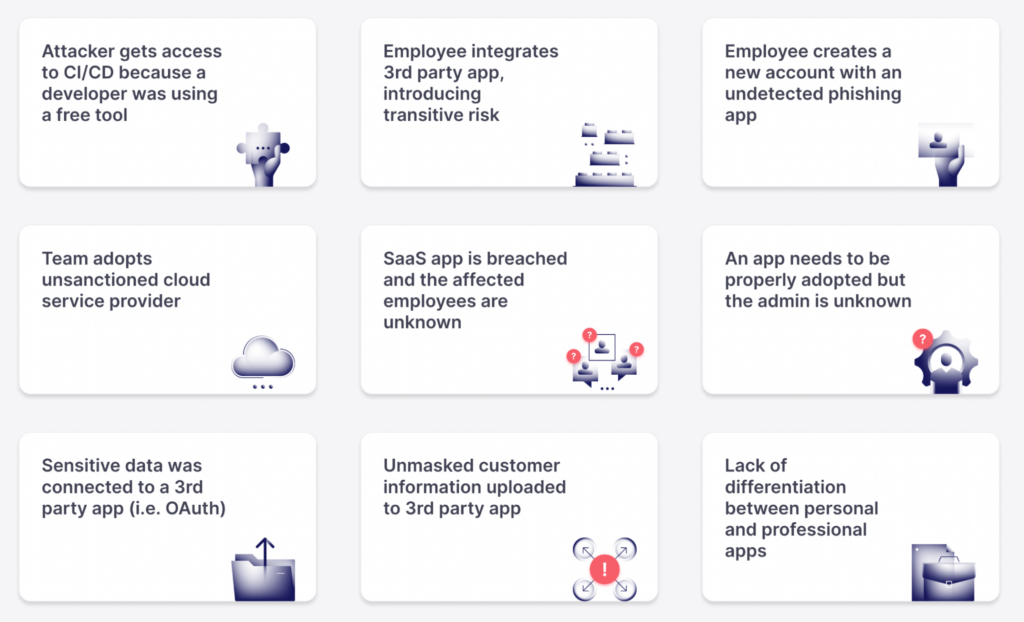
 ITGuardian provides a more comprehensive overview of how that eventual breach works here.
ITGuardian provides a more comprehensive overview of how that eventual breach works here.
While not every shadow IT solution will end up as tragic as Codecov, nearly all solutions require some access to corporate data or computing infrastructure. There are few, if any, companies that are comfortable with governance around risk to be bypassed in order to facilitate a “consumerized” go-to-market approach. Most CISOs consider shadow IT to be a time bomb of unknown magnitude that will eventually blow up.
 Gartner defines this “Consumerization of IT” trend in its IT Glossary in the following manner:
Gartner defines this “Consumerization of IT” trend in its IT Glossary in the following manner:
“Consumerization is the specific impact that consumer-originated technologies can have on enterprises. It reflects how enterprises will be affected by, and can take advantage of, new technologies and models that originate and develop in the consumer space, rather than in the enterprise IT sector. Consumerization is not a strategy or something to be “adopted.” Consumerization can be embraced and it must be dealt with, but it cannot be stopped..” – Gartner
So what’s not to like about employees finding useful tools that help them get work done and using them for free or for a minor monthly fee? Well, for starters there can be serious security issues introduced into the enterprise. In the case of Codecov, to help you test your code, it needed access to your code – all of it. For all but a few companies, “all of your code” represents an enormous collection of intellectual property. Most companies have all sorts of policies and controls protecting things like that. A company like Codecov may spend weeks, or even months working through all these policies and ensuring they can be trusted were they to approach the company directly. By sidestepping that and going directly to the employees, all that friction to productivity is avoided. What could go wrong?
This is frightening indeed. It would be simple to say, “Shadow IT is bad, we simply will not allow it.” The problem with that is that shadow IT is the symptom of a change that is not exclusively a problem. The change is in the way we work. When we go online to find solutions and a company appears that solves our problem for free, “we” (most all human beings aside from a few security people) will use it.
For most of us, this is actually a wonderful new world: I run into a problem, I search for solutions, I find it, I buy it, I use it, I get my work done, productivity goes through the roof. Of course, the IT department doesn’t see the world that way. “We build a network and we buy you the tools, and you use these tools, and you’re productive.” This stalemate cannot persist and it will not end with either of the parties having absolute say over the other. It’s obvious that employees cannot go out into the market and bring new technology in without any governance or oversight. But the alternative of just shutting it down is equally flawed. Prohibiting the current generation of workers from being intuitive, curious and productive might work in some rare settings, but sooner than later that approach will wind up with all your employees leaving and working somewhere else. Somebody needs to bridge this gap.
Enter the Nudge Solution
Nudge Security’s solution provides a simple and comprehensive method for companies to continually discover, analyze and manage shadow IT services that make their way into the modern enterprise. They have developed the first-ever SaaS security solution to discover shadow IT and curb SaaS sprawl across devices and locations. Nudge Security also does what previous enterprise security solutions have failed to do: make employees core to the solution.
 Nudge Security can be trialed online and provides results within minutes. The product utilizes a novel method of analysis which provides a high degree of accuracy and context. It is able to mine metadata and application behaviors in order to develop a clear picture of who has signed up for what services, how they propagate and how they are being utilized. This is all done without the need for network monitoring, agents or browser plugins.
Nudge Security can be trialed online and provides results within minutes. The product utilizes a novel method of analysis which provides a high degree of accuracy and context. It is able to mine metadata and application behaviors in order to develop a clear picture of who has signed up for what services, how they propagate and how they are being utilized. This is all done without the need for network monitoring, agents or browser plugins.
Once this initial analysis has been performed, a more comprehensive analysis of the service for security vulnerabilities and proper configuration is made to determine relative risk and the specific use within the enterprise. It is one thing to know that a service is being used, even better to know who is using it, but ultimately most useful to determine the risks and best practices for mitigation.
This is great, but few organizations are staffed and budgeted adequately for just the small number of applications that are sanctioned and managed by the company. What happens when the number of applications used explodes due to the impact of shadow IT? A few of the services employees bring to work can be ignored (or sent home) such as online dating, stock trading or other strictly personal applications. But the ones used to manage the business? Those are now part of the supply chain; they hold proprietary information and critical corporate data. Numerous governance requirements and common sense dictates that they must be managed. Where will the headcount and budgets for that come once these applications are discovered?
First of all, that day is now. When Nudge Security comes into companies, they always ask, “How many solutions do you think your employees are using to get their jobs done?” The average answer is around 35. And they typically find hundreds in use. The initial reaction for many companies is: “Well they can’t do that, we will just shut it down.” This is unlikely to work. Remember when we talked about friction versus security, employees figuring stuff out, solving problems, getting stuff done? Good luck to the security executive that champions friction, inefficiency and turning off tools that are making employees productive and happy. This is where the true value of nudging can be found (and it’s the inspiration for the company’s name). Nudge Security helps security teams recruit an army to help with this work – the employees (who created the problem) will help solve the problem.
The name Nudge Security comes from the behavioral psychology “nudge theory.” The idea is that rather than to try to say “no” to everything, and have your employees leave, what if you were able to give them little nudges?
“We see you’re using this new product. That’s awesome! Do you mind answering a simple question so we can put it in our supply chain management system?”
Now we know this new vendor is a vendor of ours. Next, let’s suggest this:
“Click here and we’re going to integrate that cool new product you’re using with our enterprise single sign-on solution.”
So, instead of putting up walls and saying, “no,” you bring things back on to the corporate estate. There’s a whole process to this that can be automated and based on specific corporate policy.
Frankly, there are some things you might find and want to tell the employee:
“You really shouldn’t be running this at work because your employers can monitor everything on their network. Let me help you get that out of the work environment and into your personal account.”
There’s stuff that comes back under corporate management, there’s stuff that goes home, there are changes to use, and there is experimental stuff that you keep an eye on.
Ongoing use of Nudge Security allows the company to identify new services as soon as they are trialed by employees. Dashboards and workflow help IT and security teams engage (or “nudge”) end users to mitigate concerns. These mitigations might result in the user no longer accessing the service from work, configuring the service to meet company standards or migrating to a company sponsored and managed solution.
Market & Differentiation
Unlike traditional SaaS security products, which were developed in order to secure company sanctioned and managed solutions, Nudge Security is solely dedicated to the discovery and management of shadow IT. The company’s initial product objectives are to provide accurate and comprehensive account discovery with 0 network configuration changes and a time-to-initial-results of less than 10 minutes.
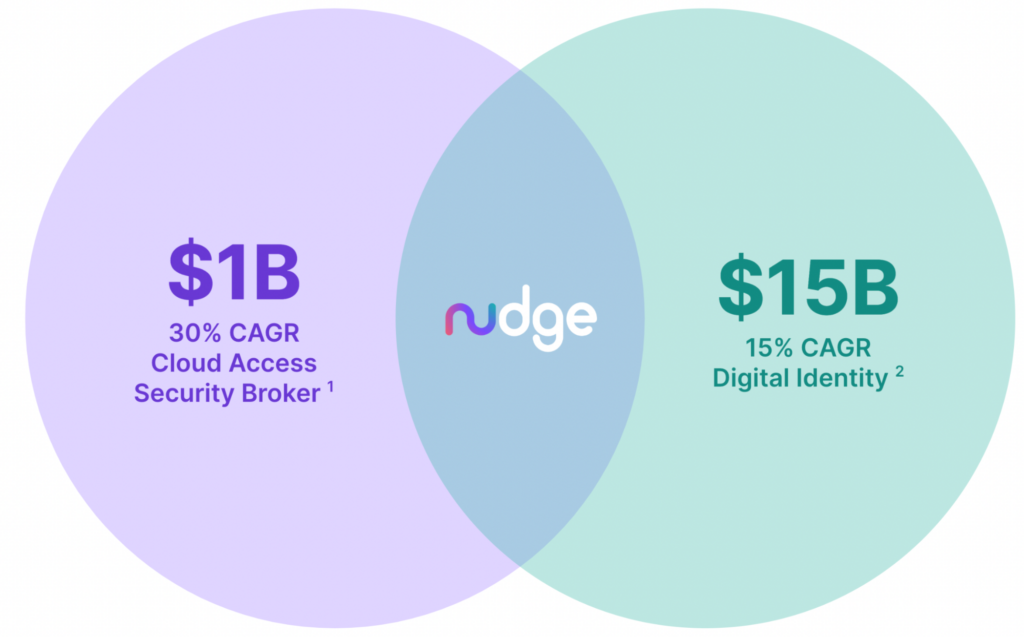
The two security markets/solutions closest to Nudge Security from a functional perspective are Digital Identity (SSO, IAM, etc.) and CASB. These solutions serve enormous TAMs with numerous large and mid-sized companies born within. However, these solutions were designed and built for the company sanctioned and managed solutions.
By their very nature they require the service to be known (and presumably sanctioned) as they must be integrated by the company. Many vendors in these markets have acknowledged and attempted to address the shadow IT concerns, but most depend on network-level interception, endpoints or browser extensions in order to discover and manage solutions. Browser-based VPN tunnels, mobile devices, BYOD and remote work all make that approach ineffective.
There are over $16B worth of products and services spent on solving the SaaS security problems associated with company sanctioned and managed solutions.
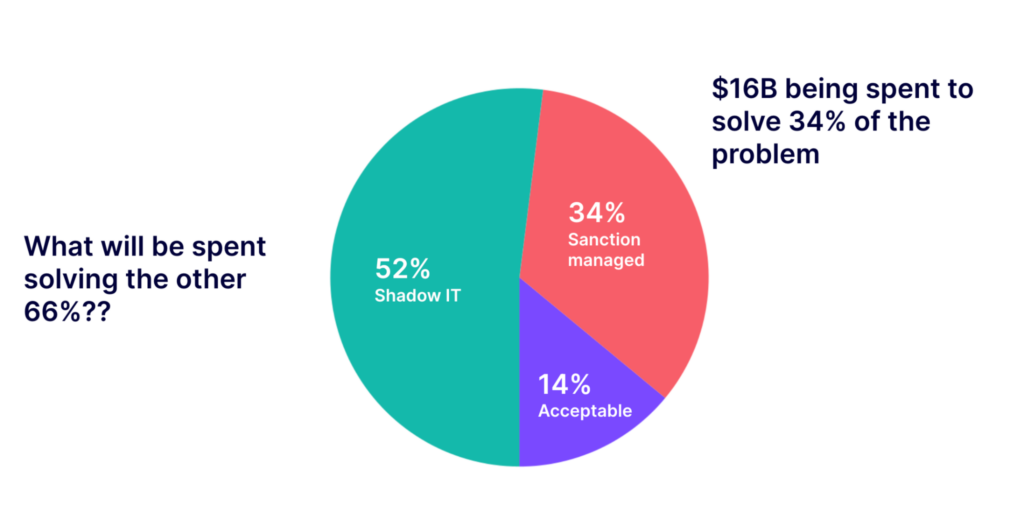 According to “The State of SaaS Sprawl in 2021” report from Productiv, company sanctioned and managed solutions represent a mere 34% of the services utilized in the typical enterprise today. If the industry is spending $16B on 34% of their productivity applications, what will they spend on the other 66%? Nudge Security intends on finding that out.
According to “The State of SaaS Sprawl in 2021” report from Productiv, company sanctioned and managed solutions represent a mere 34% of the services utilized in the typical enterprise today. If the industry is spending $16B on 34% of their productivity applications, what will they spend on the other 66%? Nudge Security intends on finding that out.
The trends fueling this phenomenon are human behavior and new go-to-market strategies that are far more efficient than traditional, costly enterprise sales models. In this new “product-led growth” approach, the end user is provided immediate access to a product for use. This results in far less friction than the traditional “enterprise sales” model of sending expensive sales teams to meet with executives. In some markets, including cybersecurity, this approach becomes a necessity as the line outside the door of the CIOs and CISOs overflows with record numbers of newly funded startups.
This distribution model pairs well with human behavior – people like empowerment and good employees like getting stuff done. Great efficiencies are derived from targeting users online and then selling directly and often providing access to the product in a free or open-source model along the way. Not surprisingly, as the consumerization trend has exploded, so has shadow IT.
We used this model with great success at AlienVault. We targeted the security engineer who would be the eventual user of the service and offered them a free trial or an open-source version of our product. Once they engaged in those experiences, we had an open channel to sell them directly through carefully crafted online content. This content guided them through initial deployment and realization of value. Once that was accomplished, they were encouraged to reach out to a sales team to place an order for a more comprehensive solution with support. Today’s IT landscape is dominated by services that either land with or exclusively utilize consumerized approaches.
 Examples include: Google Workspace, Skype, AWS, Splunk, Dropbox, Marketo and countless others.
Examples include: Google Workspace, Skype, AWS, Splunk, Dropbox, Marketo and countless others.
This go-to-market approach has provided enormous benefits for the solution provider that can develop a superior product and perfect the approach – you can no longer win with bottles of wine, rounds of golf and fancy dinners. You have to get your product in the hands of the user – and it has to provide value.
So what is the problem with such an efficient and democratic model of distribution? Well, as you bypass the executives and cumbersome acquisition processes, you also bypass corporate governance. Some of that governance, managed by the CISO, protects the company from risk. When a well-managed company acquires new solutions, great care is taken to vet the new solution for all sorts of risks that may harm the company or its constituents.
Wouldn’t it be great if companies could have both? All it takes is a nudge!

